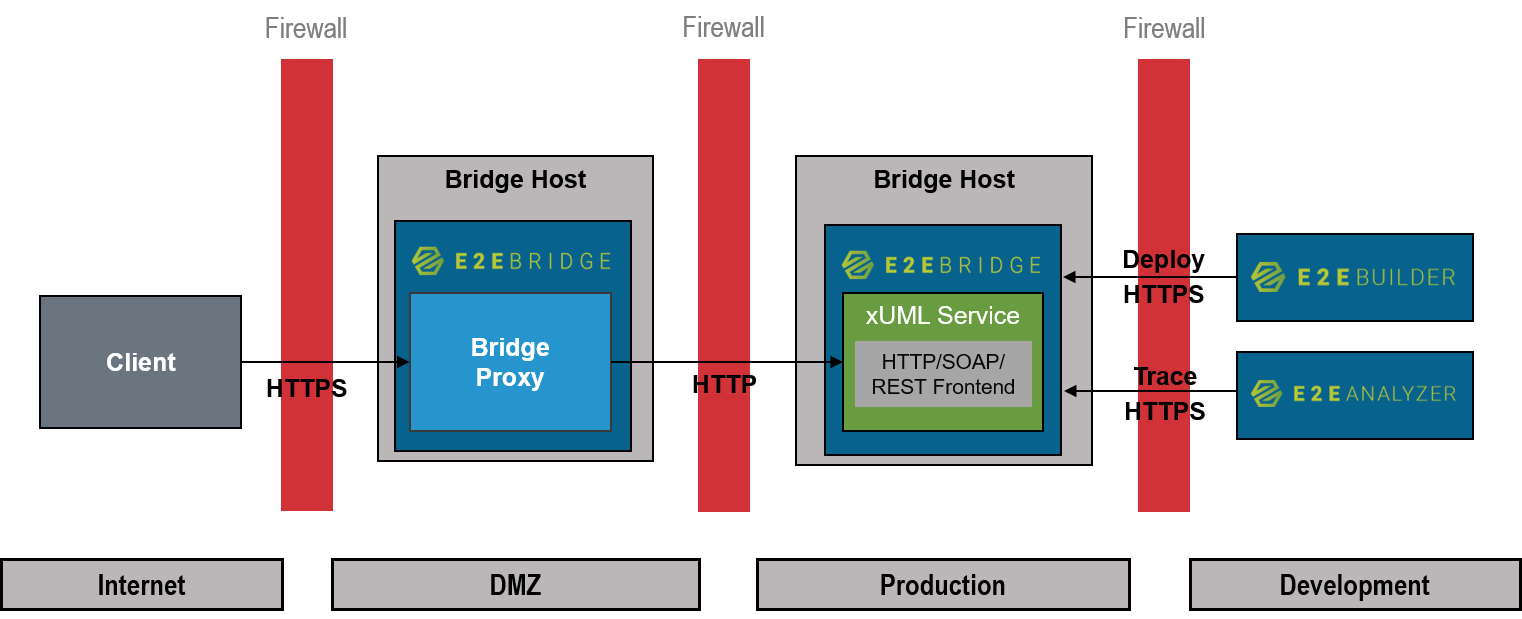
The Bridge supports the use of proxies. The Apache HTTP Server including the appropriate modules has been installed together with the Bridge. The Apache proxy can be used as reverse proxy in front of Bridge SOAP or HTTP frontend services.
The proxies are defined in the deployment diagram of a UML model in MagicDraw. Proxy servers can be run on the same node instance as the Bridge or on a dedicated node instance. If the proxy is run on a dedicated node instance, the node instance must have installed Bridge and it must be member of the same Bridge domain as the node instance, to which the service is deployed. When you deploy a service including proxy definitions, the Apache proxy is started on the defined node instance automatically.
A Bridge Proxy Server certificate enables encrypted secure communication and user authentication via the Apache proxy ().
When installing the Bridge, a self-signed default SSL certificate will be installed. See chapter Importing and Exporting Proxy Server Certificates for detailed information of how to enroll and install an official certificate from a certificate organization.
With regard to authorization, Bridge Proxy Server supports, for example, file based authentication or external authentication validation databases, such as LDAP and SQL RDBMS.
In the picture below, a possible architecture is displayed. In this example, a proxy instance runs on a dedicated node instance. Client requests will be routed to the frontend services of the service.
Figure: Example Proxy Architecture
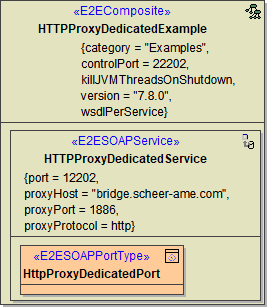
The component diagram of the example above is shown below.
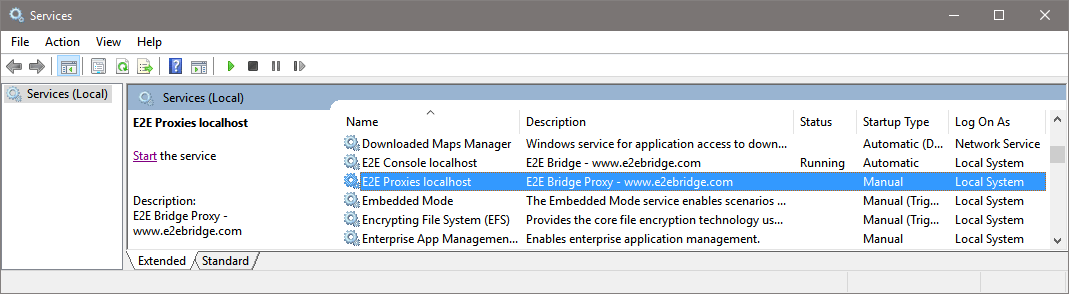
In the Windows Services tool, you can find a service entry E2E Proxies. This service controls the Apache HTTPD and is managed from the Bridge. When a proxy service is started or stopped with the Bridge, the E2E Proxies service will be started or stopped automatically.
The Bridge provides the following proxy management functions:
