Page History
...
- You can use a key pair in format PKCS#8 (generated e.g. by OpenSSL). In this case, you do not need to generate a key pair with the E2E Bridge and you can proceed with the next steps.
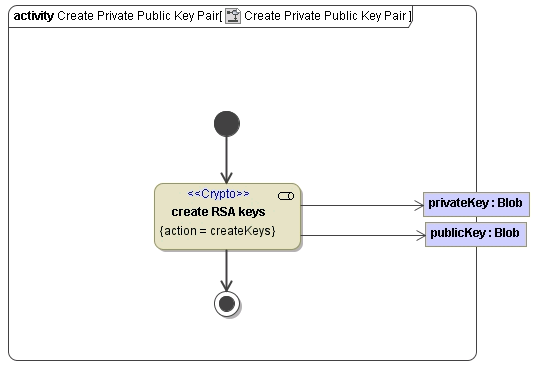
- You can use the E2E Bridge to generate a private/public key pair in format PKCS#1. This can be done via the action createKeys. The adapter does not need any input but creates two Blob objects named privateKey and publicKey.
The following figure shows the necessary activity diagram to create the private and public keys in format PKCS#1.
Figure: Create RSA Keys Example
With this pair of keys it is possible to identify the sender of any data.
...
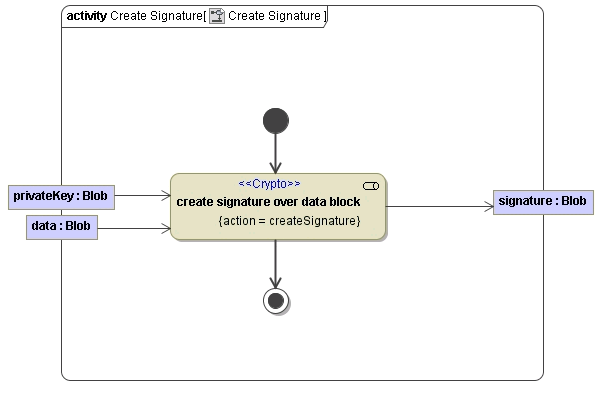
The following action node adds the privateKey to the data object and creates the object signature containing the data.
Figure: Create Signature Example
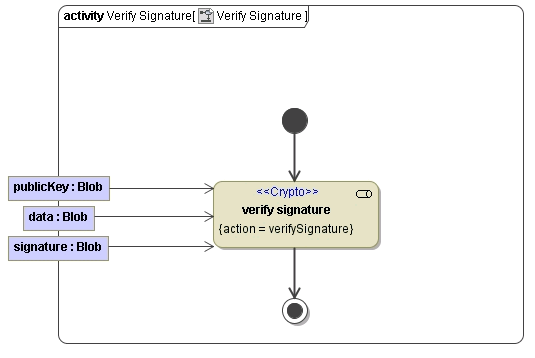
Validating a Signature
To check if the created signature is valid, you can use action verifySignature. This action takes a signature, the corresponding public key and data blob and returns an error message like "Verifying signature failed.", if one parameter is not valid or does not correspond to the others.
You do not have to specify the key format. The Runtime will try to read the public key as PKCS#8. If this fails, the Runtime will re-try to read the public key as PKCS#1.
The following figure shows how to verify a signature:
Figure: Verify Signature Example
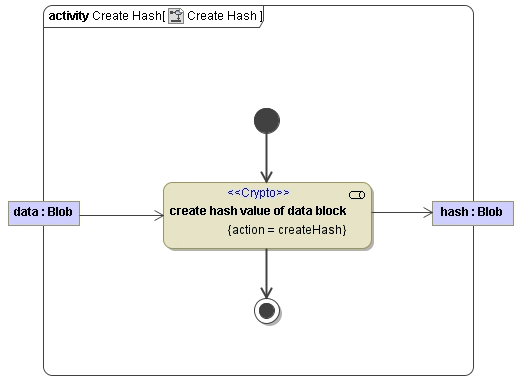
Hashing Data
Sometimes it is desirable to get a hash value of a given blob. This is done using an action node having the stereotype <<Crypto>> and the action createHash.
Builder 7.12.0 The Crypto adapter uses the hash algorithm specified with parameter algorithm, or the digestAlgorithm specified on the <<Crypto>> action node if no parameter has been supplied. If no algorithm is supplied at all, the adapter uses default algorithm sha1.
Refer to the Crypto Adapter Reference for more details.
The Crypto Adapter is using the SHA-1 algorithm. For further information about SHA-1 please refer to http://en.wikipedia.org/wiki/SHA-1. The following figure shows how to create a hash :Figure: Create Hash Examplewith the default algorithm: