To configure the RESTifier for SAP, click the configuration icon in the top-right corner and select one of the menu entries. You can configure
If you can't find the appropriate menu items or if you're missing the configuration icon at all, refer to section Configuring Users and Permissions.
Permissions
To use the RESTifier for SAP, the SAP user the RESTifier uses to access your SAP system must be allowed to execute the following RFCs (also see Configuring the SAP Connection below):
-
BDL_FUNCTION_INTERFACE_GET
-
DDIF_FIELDINFO_GET
-
RFC_FUNCTION_SEARCH
-
RFC_GET_FUNCTION_INTERFACE
-
RFCPING
-
SDIXML_FIELDINFO_GET
Configuring the SAP Connection
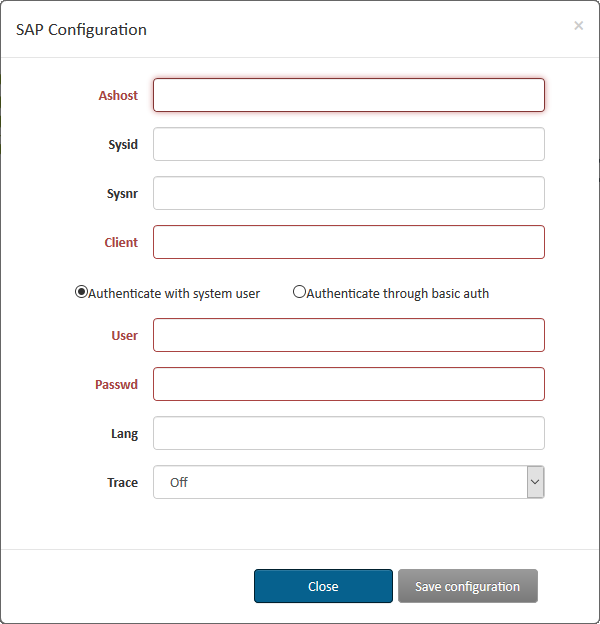
Configure the standard SAP connection parameters here. In case of connection problems, double-check if the given values are correct.
Fields marked red are obligatory. You cannot save the configuration without having set these values This dialog will also pop-up on every page load if the configuration is incomplete.
By selecting Authenticate through basic auth, you can enable a mode that allows to pass SAP credentials with each request. This mode enabled, authentication is required for RFC execution and metadata. Pass these credentials via standard BasicAuth headers:
Trace Settings
You can set the following Trace values:
|
Name |
SAP Value |
|---|---|
|
Off |
0 |
|
Brief |
1 |
|
Verbose |
2 |
|
Full |
3 |
Please keep in mind, that high trace levels may produce very big log files. It's recommended to keep tracing off unless you're investigating problems. When trace is enabled, SAP libraries will generate a bunch of *.trc files in the working directory. The content varies depending on the trace level from overview of the API calls to hexadecimal dumps of the actual data being processed.
After changing the Ashost parameter, it's highly recommended to rebuild the search cache.
Configuring Connection Pooling
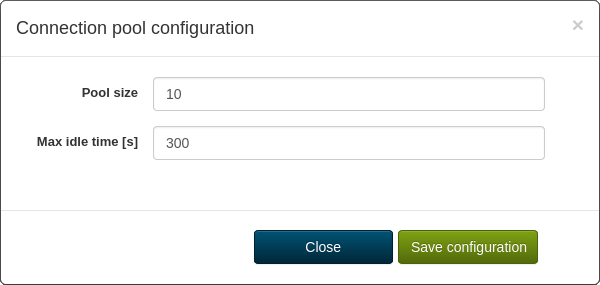
The RESTifier uses connection pooling for better performance:
|
Pool Size |
The maximum number of parallel connections the pool will hold. The actual connection count may be less but will never exceed the given value. |
|---|---|
|
Max idle time [s] |
The longest time the connection can remain in the pool unused. If the connection remains unused longer, it'll be closed. |
Configuring Performance Options
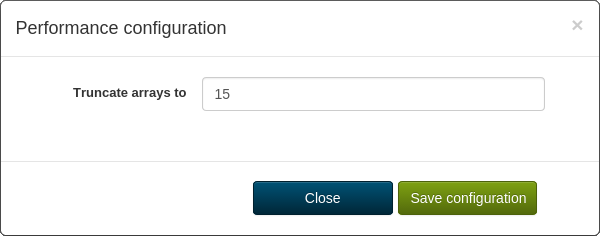
Some BAPIs may return really large arrays. At some point, browser may hang or even crash trying to process such data. This option reduces the size of the array to about the given size. If there are any elements removed, they will be replaced by a string describing how many elements were omitted. After this string, there will be the last element of the array:
Rebuilding the Cache
As interaction with SAP system is generally slow, the RESTifier uses caching to provide a real-time instant search. The drawback is that whenever you add or remove a BAPI from SAP system, you have to rebuild the RESTifier's cache. The procedure boils down to clicking Rebuild cache in the configuration menu of the RESTifier and can take up to several minutes depending on the speed of SAP system and the connection. It doesn't require restarting the service.
There's also a secondary cache managed by the SAP library which cannot be simply rebuild. That means a restart of the RESTifier may be required after altering BAPI's parameter list in order to pick the new metadata.
Configuring the Logging
The Log level sets the verbosity of internal logging. The default value Info should be appropriate for a production system. Everything more verbose (Verbose, Debug, Full) may cause a significant grow of the logs. The setting is only applied to the log files:
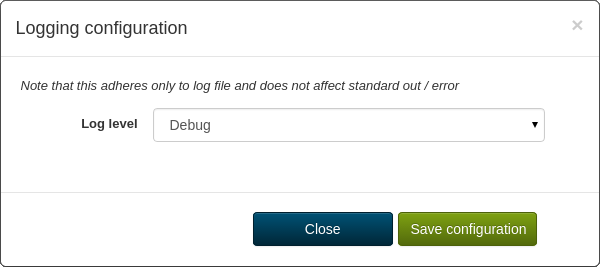
|
Destination |
Log Level |
|---|---|
|
standard output |
Info |
|
standard error |
Error |
|
logfile |
User-specified |
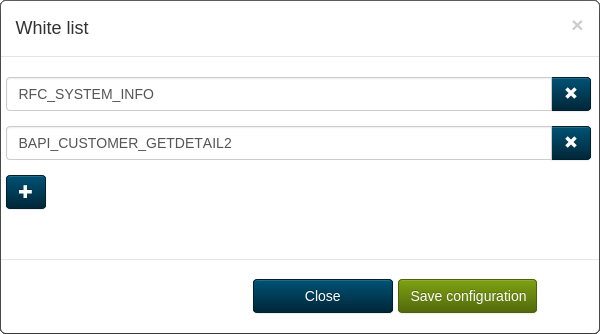
Configuring a BAPI White List
Defining a white list allows you to configure the BAPIs each user will be able to call. Use option Plus to add another entry and type BAPI's name exactly. Use option X next to a list entry to remove it from the list. Refer to section White List for more information:
Configuring Users and Permissions
The RESTifier can be used with the E2E Auth Server to provide application-level permission control. The user management is being done using E2E Auth Server's administration panel. The RESTifier then refers to the role a user has been assigned to.
Roles
There are two roles the RESTifier is aware of:
|
SapRestifier-Api |
user having this role is allowed to search, get metadata for and execute all BAPIs |
|---|---|
|
SapRestifier-Admin |
user having this role can additionally modify RESTifier's configuration (has access to the /config API) |
A user that has none of the above roles and an anonymous user can search and get metadata for all BAPIs, but can only execute the white listed ones.
White List
The set of BAPIs that can be executed by any (including anonymous) user is called the white list. To configure it, you have to have user support already turned on. As a user with SapRestifier-Admin role use the menu entry White list to compose a list of BAPIs you want to allow for anyone to call. Trying to call a BAPI from outside the list will result in a 401 HTTP response.
Enabling User Support
By default user support is turned off, meaning that everyone can do anything. To have better control you may want to enable it. To avoid a chicken-egg problem, the settings are not exposed in the UI. We strongly recommend using the Bridge to change those settings, although they can be edited with any text editor (please refer to config/default/config.json and copy and edit the "e2eAuth" section of configuration).
Menu
The menu differs depending on the logged-in user and user control configuration. Except for Documentation and Rebuild cache, all menu entries open a corresponding setting dialog (see top of the page for more information).
|
User Control Enabled |
User Control Disabled |
|---|---|
|
If user control is disabled, the menu looks like this: 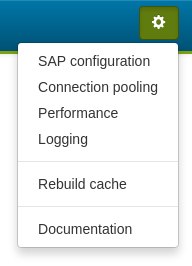
The only difference is the lack of the menu item White list. |