Basic Authentication
This policy enables HTTP Basic Authentication on an API. You can use this policy to require clients to provide HTTP BASIC authentication credentials when making requests to the managed API.
Configuration Options
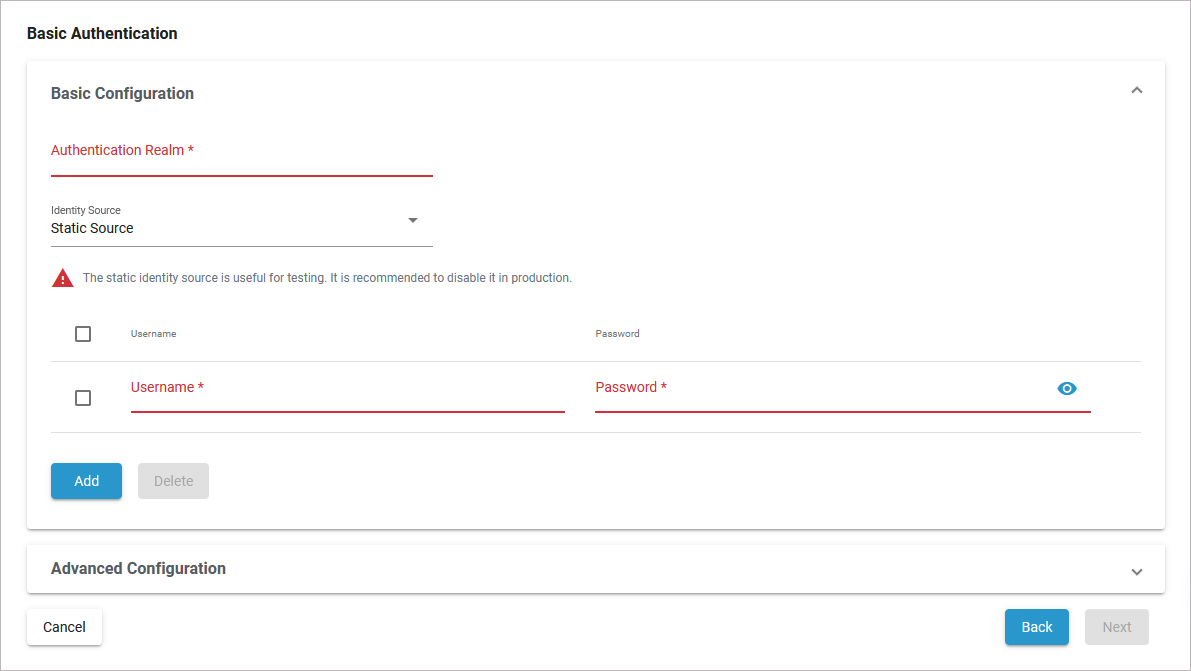
Basic Configuration
Option | Description | Possible Values | Default |
|---|---|---|---|
Authentication Realm | Defines the Basic Auth realm that will be used when responding with an auth challenge (when authentication is missing or fails). The input of a realm is mandatory. | a string | - |
Identity Source | Additionally, one of the complex properties must be included in the configuration, indicating whether API Management should use JDBC, LDAP or Static information as the source of identity used to validate provided user credentials. Configuration details of the identity source are listed in the table below. | Static Source |
Identity Source Configuration Options
Identity Source | Content | Description | Possible Values | Default |
|---|---|---|---|---|
Static Source | ||||
|
Not recommended for production. Use Keycloak OAuth or JWT instead. | Username / Password | Allows you to provide a static set of user names and passwords. | - | - |
Click Add to create more rows in the table. Click Delete to remove selected rows. | ||||
JDBC | ||||
|
Only PostgreSQL, MariaDB and MySQL are supported. | URL | The URL to the JDBC server. | a string | - |
JDBC URL | The URL to the JDBC database. | a string | - | |
Username | The username to use when connecting to the JDBC database. | a string | - | |
Password | The password to use when connecting to the JDBC database. | a string | ||
SQL Query | If Also extract user roles from the DB is true: SQL query to use when extracting role information. The first parameter passed to the query will be the username. | a string | - | |
Password Hash Algorithm | The hashing algorithm used when the password was stored. |
| SHA1 | |
Also extract user roles from database | Enable this option if you also want to extract role information from the database. |
| disabled | |
Roles SQL Query | If Also extract user roles from database is enabled: | a string | - | |
Advanced Configuration
Option | Description | Possible Values | Default |
|---|---|---|---|
Forward Authenticated Username as HTTP Header | Indicates the name of an HTTP header to send with the principal/identity of the authenticated user if authentication succeeds. Useful when the backend API needs to know the identity of the authenticated user. | a string | - |
Related Pages:
