The JWT Policy helps you to validate JSON Web Tokens (JWT) by providing a signing key or a JSON Web Key Set (JWK(S)). You can also require claims and strip them to forward them as header to the backend API.
Configuration Options
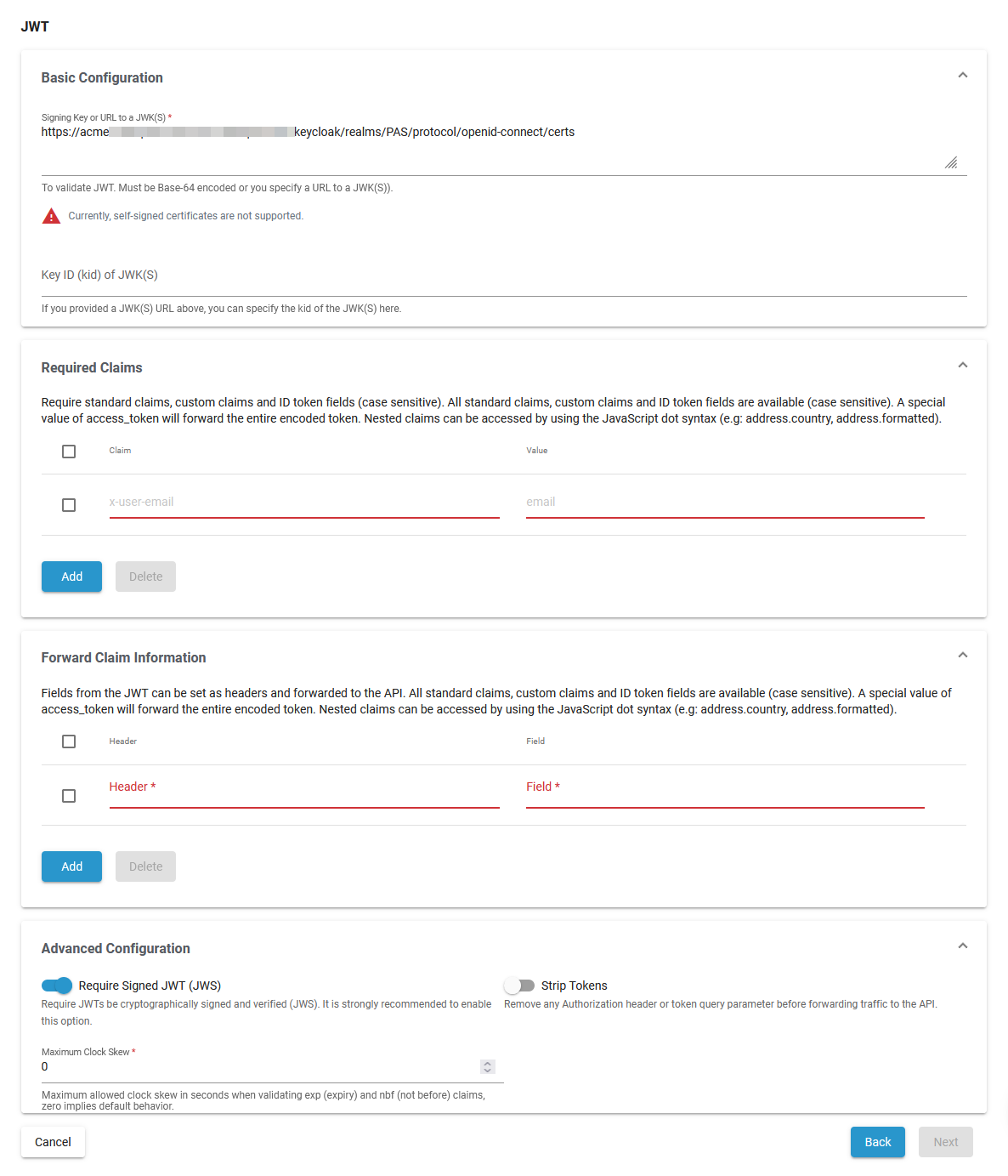
Basic Configuration
| Option | Description | Possible Values | Default |
|---|---|---|---|
| Signing Key or URL to a JWK(S) | Specify a Base-64 encoded signing key or a URL to a JWK(S) to validate JWT. |
| FQDN path automatically set for your PAS installation |
| Key ID (kid) of JWK(S) | Specify the key id of the JWK(S) in this field if you provided a JWK(S) URL. | a valid string | - |
Required Claims
| Option | Description | Possible Values | Default |
|---|---|---|---|
Claim | Specify a list of required claims. If a required claim is not present, access will be rejected. | a string | - |
Value | Determines the content of the claim. | a string | - |
Forward Claim Information
Fields from the JWT can be set as headers and forwarded to the API.
| Option | Description | Possible Values | Default |
|---|---|---|---|
Field | Specify a list of fields from the JWT to be forwarded to the API as a header. | a string | - |
| Header | Holds the value of the Field. | a string | - |
Advanced Configuration
| Option | Description | Possible Values | Default |
|---|---|---|---|
| Require Signed JWT (JWS) | Specify whether JWTs must be cryptographically signed and verified (JWS). |
| enabled |
| Strip Tokens | Enable if the Authorization header or token query parameter should be removed before forwarding traffic to the API. |
| disabled |
| Maximum Clock Skew | Specify the maximum allowed clock skew in seconds when validating exp (expiry) and nbf (not before) claims. 0 implies default behavior. | a valid integer | 0 |