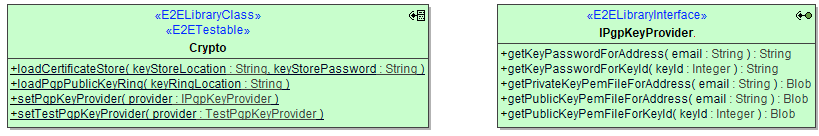
For some functionality the library needs to know about certificates and keys:
- Verification of secure connections
To verify secure connections (SSL/TLS/HTTPS) to mail servers, the underlying JVM must know the certificate chain. If you get errors indicating that the SSL handshake fails due to certificate errors, most likely the JVM can not verify the certificate sent by the mail host.
You can fix this by either- importing the certificates (or all missing certificates of that certificate chain) into the JVM's keystore so they can be found automatically by the JVM.
- importing them into a separate Java Key Store (JKS). Only in this case you need to load this separate keystore by means of loadCertificateStore().
- Verification of PGP signatures
To verify PGP signatures, the public key of signers must be known. To do this, you can load a PGP public key ring into the library. Refer to you PGP installation about how to export public keys.
Operations
loadCertificateStore
| Parameter | Types | Direction | Description | Allowed Values / Example | |
|---|---|---|---|---|---|
| keyStoreLocation | String | in | Specify the path to the keystore file. | opt/bridge/crypto/mailservercerts.jks | |
| keyStorePassword | String | in | Specify the password of the keystore. | ||
loadPgpPublicKeyRing
to be discontinued Future versions of the library will rely on setPgpKeyProvider() solely (see below), this operation will disappear. Until then it is still required if you want to verify signatures of unencrypted emails.Parameter Types Direction Description Allowed Values / Example keyRingLocation String in Specify the path to the keyring file. opt/bridge/crypto/pubkeys.asc
Overview
Content Tools