Page History
Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
The IP Blocklist Policy blocks access to the resource of an API based on the IP address of the client. Users are able to use wildcard characters in specifying the IP addresses to be blocked. In addition, you have the option of specifying the return error code sent in the response to the client if a request is denied.
| Multiexcerpt include | ||||||||
|---|---|---|---|---|---|---|---|---|
|
| Info |
|---|
Before PAS 22.1.1 the name of this policy was IP Blacklist. Existing policy configuration will be shown with the old name. |
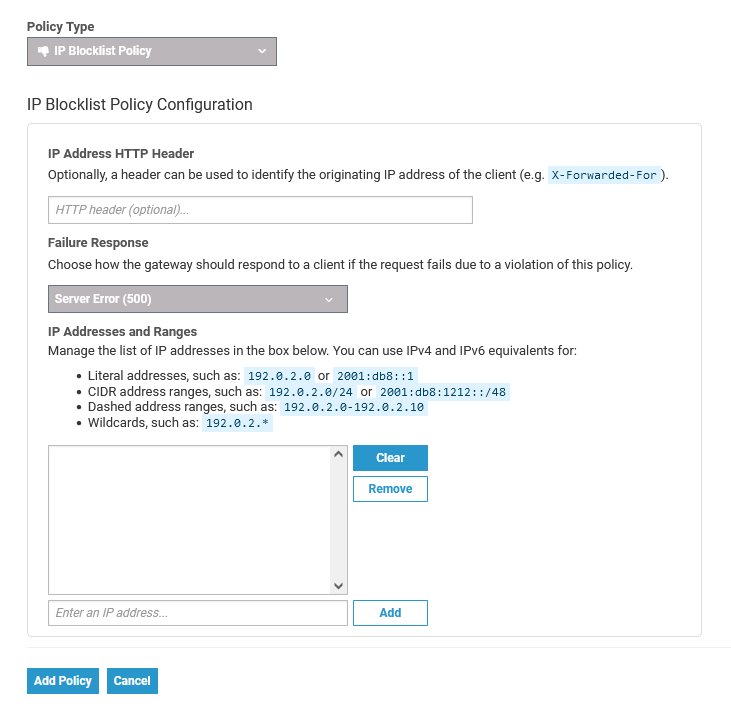
Configuration Options
| Option | Type | Description | Possible Values | Default | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| IP Address HTTP Header | String | Optional. Tells the API Management to use the IP address found in the given HTTP request header instead of the one associated with the incoming TCP socket.
| - | - | ||||||||
| Failure Response | Enum | The server response code. | Authentication Failure (403) Not Found (404) Server Error (500) | None | ||||||||
| Enter an IP address | Array[<ipList>] | The IP address(es), and/or ranges of addresses that will be blocked from accessing the API. IPv4 and IPv6 are supported. |
| - |
| Panel | ||
|---|---|---|
| ||
|
| Panel | ||
|---|---|---|
|
| Otp | ||||
|---|---|---|---|---|
|