Page History
Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
| Multiexcerpt include | ||||||||
|---|---|---|---|---|---|---|---|---|
|
Prerequisites
Please consider the following prerequisites regarding Scheer PAS API Management.
| Multiexcerpt include | ||||
|---|---|---|---|---|
|
Step 1: Download and Extract the Software
| Multiexcerpt | ||
|---|---|---|
| ||
API Management uses Docker to provide a simple setup which is easy to update and scalable if necessary. |
| Note |
|---|
Make sure you have network access during the installation, because you have to download images from Docker hub. |
Download the following files provided by Scheer to the folder you want to install API Management to:
api-mgmt-<VERSION>.zip
api-mgmt-devportal-<VERSION>.tar API Mgmt 7.6.0
api-mgmt-gateway-<VERSION>.tar
api-mgmt-keycloak-<VERSION>.tar
api-mgmt-ui-<VERSION>.tarTip Later on, in step 6, you will need file apiman-default-config.json from archive api-mgmt-<VERSION>.zip on an API Management client, so copy the ZIP file to your client now (or later).
Extract api-mgmt-<VERSION>.zip.
Extracting this file will create a folder api-mgmt which is required permanently. It contains configuration files with sensitive data such as passwords, so access to this folder should be restricted. The Docker container however must be able to read the data.Load the Docker images:
Multiexcerpt include MultiExcerptName load_docker_images_api PageWithExcerpt INTERNAL:_installation_excerpts
| Anchor | ||||
|---|---|---|---|---|
|
Configure the installation settings in the Docker .env file as described below. This file resides in folder api-mgmt\single-host-setup\.
| Info |
|---|
.env is a hidden file. |
| Setting | Description | Default Value | Since Version | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
BRIDGE_URL | Provide your BRIDGE hostname(s). You may specify more than one URL as a comma-separated list.
| bridge.acme-corp.com | |||||||||||
BRIDGE_PORT | Provide the BRIDGE port(s). If you have added a list of BRIDGE URLs with setting
| 8080 | API Mgmt 7.3.0 | ||||||||||
BRIDGE_USERNAME | Provide the user name to access your BRIDGE.
| username | |||||||||||
BRIDGE_PASSWORD | Provide the password to access your BRIDGE.
| password | |||||||||||
DEV_PORTAL_PORT | Provide the port to access the user interface of the API Management Developer Portal. | 8447 | API Mgmt 7.6.0 | ||||||||||
ELASTICSEARCH_JAVA_MEMORY | Provide the amount of memory that Elasticsearch can allocate.
| 2g | |||||||||||
ENDPOINT | Provide the hostname of your API Management HOST.
| api.acme-corp.com | |||||||||||
GATEWAY_PORT | Provide the port to access the published APIs. | 8444 | |||||||||||
KEYCLOAK_ADMIN_USERNAME | Define a Keycloak user. | username | API Mgmt 7.3.0 | ||||||||||
KEYCLOAK_ADMIN_PASSWORD | Set a password for the Keycloak user. | password | API Mgmt 7.3.0 | ||||||||||
KEYCLOAK_PORT | Provide the port to access Keycloak. | 8445 | |||||||||||
KIBANA_ENCRYPTION_KEY | Set a key to encrypt cookies. You should change the default value to an alphanumeric string with 32 characters.
| J844Az3f0s74IiUepVgfX0XqqH1hcUyK | API Mgmt 7.4.0 | ||||||||||
KIBANA_PORT | Provide the port to access Kibana.
| 8446 | API Mgmt 7.4.0 | ||||||||||
MYSQL_PASSWORD | Set a password for the Keycloak database connection. | password | |||||||||||
MYSQL_ROOT_PASSWORD | Set a root password for the MySQL installation. | root_password | |||||||||||
SELF_SIGNED | Specify certificate usage.
| true | |||||||||||
TRUSTSTORE_KEYSTORE_PASSWORD | Provide the password of the Java truststore file that contains the certificates. This password will also be used if you create a keystore with our script to generate self-signed certificates (see section Use Self-Signed Certificate below).
| secret | |||||||||||
UI_PORT | Provide the port to access the API Management user interface. | 8443 |
| Anchor | ||||
|---|---|---|---|---|
|
Overview on the Docker Setup of API Management
Have a look at the figure below to get a technical overview on the Docker setup of Scheer PAS API Management.
 Image Removed
Image Removed
Overview on the Installation Containers
| Note |
|---|
The three mentioned ports should be available. Otherwise you have to adapt the configuration files. |
Overview on the Installation Process
To install the Scheer PAS API Management, you need to got through the following steps:
API Management uses Docker to provide a simple setup, which is easy to update and scalable if necessary.
For a description on how to load and run the Docker files, refer to Setting up API Management.
An overview of the values that have to be configured is shown on page Configuring API Management.
| Multiexcerpt | ||
|---|---|---|
|
You need a certificate to establish secure connections between |
clients and API Management, as well as between the different components of API Management itself. You can use an official certificate, or you can create a self-signed one. |
| Tip |
|---|
We recommend using an official and valid certificate. |
| Info |
|---|
Folder api-mgmt\configs already contains an example structure of the needed files. |
| Note |
|---|
This setup is designed to run on one host only. The SSL KeyStore is shared between all services. |
Use Official Certificate
To use your official certificate, proceed as follows:
- Copy apiman.jks and the tls files of your certificate (tls.crt and tls.key) to folder api-mgmt\configs (see example structure).
Create a Java keystore which includes the certificate. The keystore must be secured by a store password. Assign the name apiman.jks to the keystore file.
Refer to Certificates and Keystores for some hints on certificate handling.Update the following entries in the Docker .env file (see table above for details):
Update entry
TRUSTSTORE_KEYSTORE_PASSWORDwith the store password.Set entry
SELF_SIGNEDto false.
If you have certificates and intermediate certificates, please consult the keycloak documentation Keycloak Docker image > Setting up TLS(SSL).
| Anchor | ||||
|---|---|---|---|---|
|
If you do not possess a valid certificate, you can create a self-signed one. You can use Java Keytool to do this.
Check the folder permissions. Docker should be able to write to the folder and execute programs in the folder (Linux folder permission
300).Generate a keystore. To do this, run the following command from folder api-mgmt/single-host-setup (folder containing the file docker-compose.
Startyml):
Code Block docker-compose run --no-deps --rm --entrypoint '/opt/api-mgmt/create-self-signed-certificates.sh' keycloakTip Some shells (e.g. git bash) have problems with the path so you may have to escape the slashes with backslash like
\/opt\/api-mgmt\/create-self-signed-certificates.sh.Copy the following generated files from folder api-mgmt/configs/ self-signed-certificates to folder api-mgmt/configs/:
apiman.jks
- tls.crt
- tls.key
| Anchor | ||||
|---|---|---|---|---|
|
| Multiexcerpt | ||
|---|---|---|
| ||
Keycloak is an open source identity and access management solution and is used to create and manage the users of API Management and OAuth2 secured APIs. |
An overview of the values that have to be configured is shown on page Configuring API Management.
You have to create the Keycloak administration user and change some of the Keycloak settings.
For a description on how to create the Keycloak administration user, refer to Setting up API Management.
An overview of the values that have to be configured is shown on page Configuring API Management.
To start API Management, you will have to start all containers.
For a description on how to start all services, refer to Setting up API Management.
Finally you can log in to Scheer PAS API Management.
Further information about the default login credentials can be found on page Setting up API Management.
Before you can start the Docker containers, you need to change some of the Keycloak settings in the Docker configuration file .env. The values you need to replace the default values with, are to be obtained from your Keycloak instance.
Start Keycloak. To do this, run the following command from folder api-mgmt/single-host-setup (folder containing the file docker-compose.yml):
Code Block docker-compose up keycloakKeycloak has been started when the log reads something like
Code Block [...] Keycloak 7.3.0 (WildFly Core 6.0.2.Final) started in 50476ms - Started 673 of 933 services [...]Multiexcerpt include SpaceWithExcerpt INTERNAL MultiExcerptName open_keycloak PageWithExcerpt INTERNAL:_installation_excerpts Change the Valid Redirect URIs of the below listed clients.
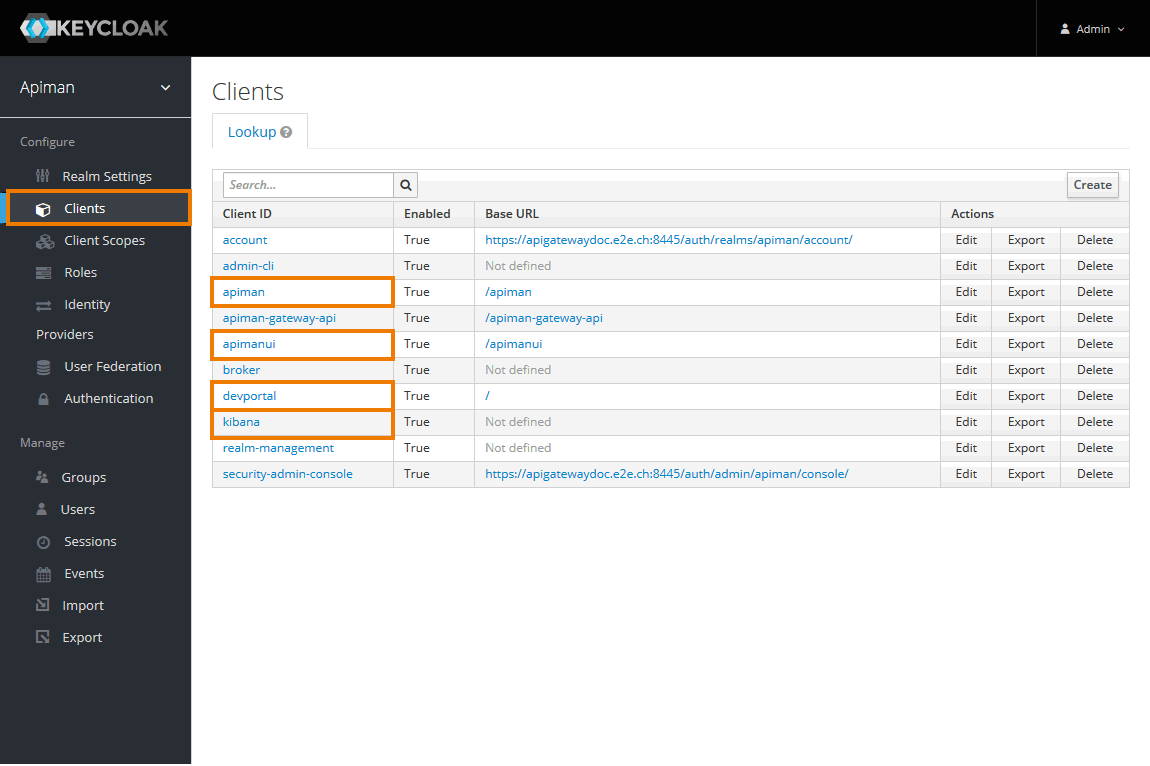 Image Added
Image AddedNavigate to Clients.
You will have to change the settings for the following clients:
- apiman
- apimanui
- devportal
- kibana
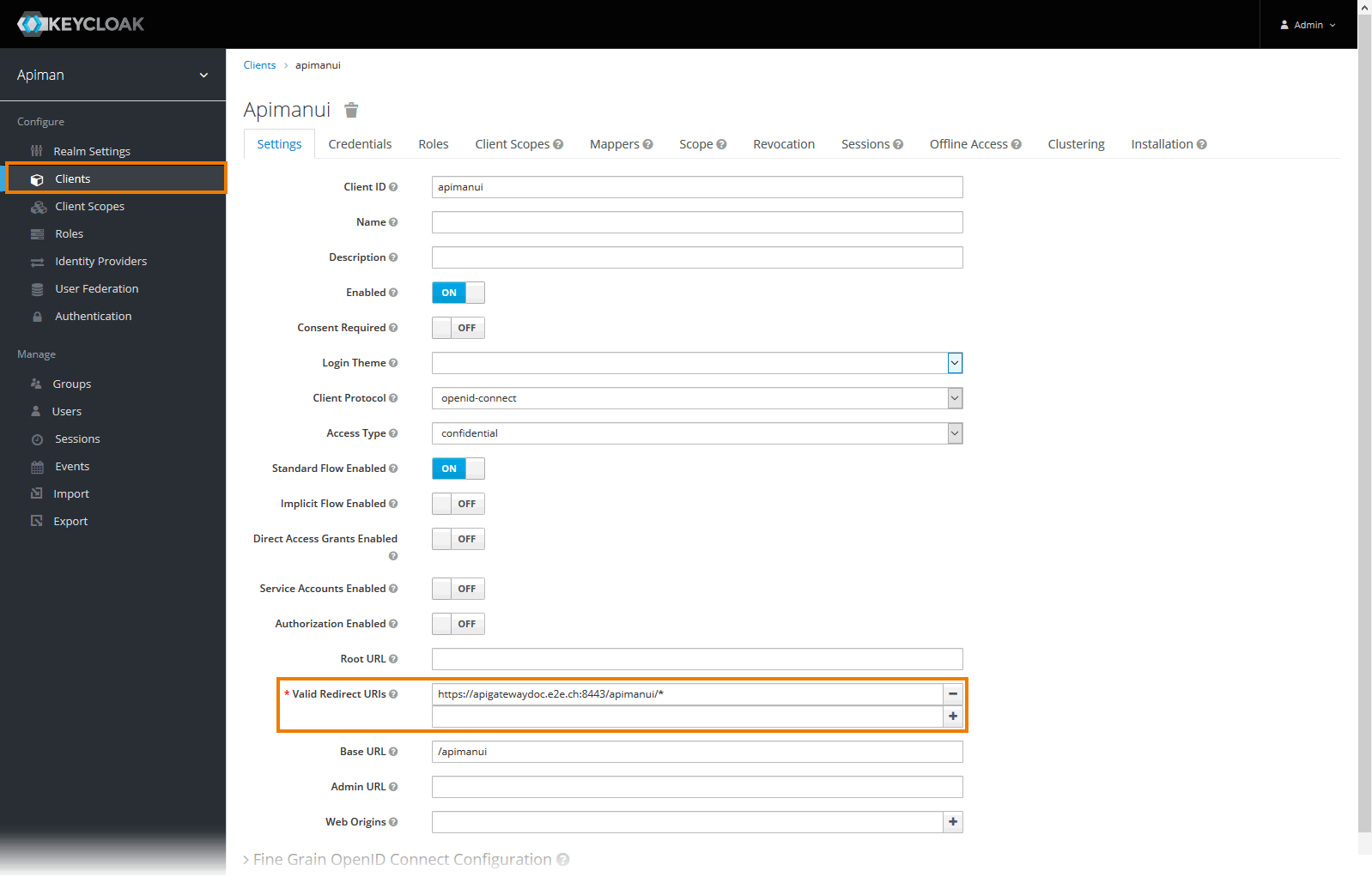 Image Added
Image AddedOpen tab Settings for each of the clients by clicking on the client ID in the list, and change the entry in field Valid Redirect URIs to match your setup:
- For client apiman, e.g.
https://api.acme-corp.com:8443/apiman/* - For client apimanui, e.g.
https://api.acme-corp.com:8443/apimanui/* - For client devportal, e.g.
https://api.acme-corp.com:8447/* - For client kibana, e.g.
https://api.acme-corp.com:8446 /oauth/callback
Now, change all default credentials for clients apiman , apimanui , apiman-gateway-api and kibana and copy the new passwords to the Docker configuration file.
Setting Description Default Value Since Version KEYCLOAK_APIMAN_SECRETProvide the secret for client apiman generated in Keycloak. passwordKEYCLOAK_GATEWAY_SECRETProvide the secret for client apiman-gateway-api generated in Keycloak.
passwordKEYCLOAK_APIMANUI_SECRETProvide the secret for client apimanui generated in Keycloak.
passwordKEYCLOAK_REALM_PUBLIC_KEYProvide the realm public key generated in Keycloak. MIGfMA0GCSqGSIb3DQEBAQU[...]KEYCLOAK_KIBANA_SECRETProvide the secret for client kibana generated in Keycloak. passwordAPI Mgmt 7.4.0 Do this as follows:
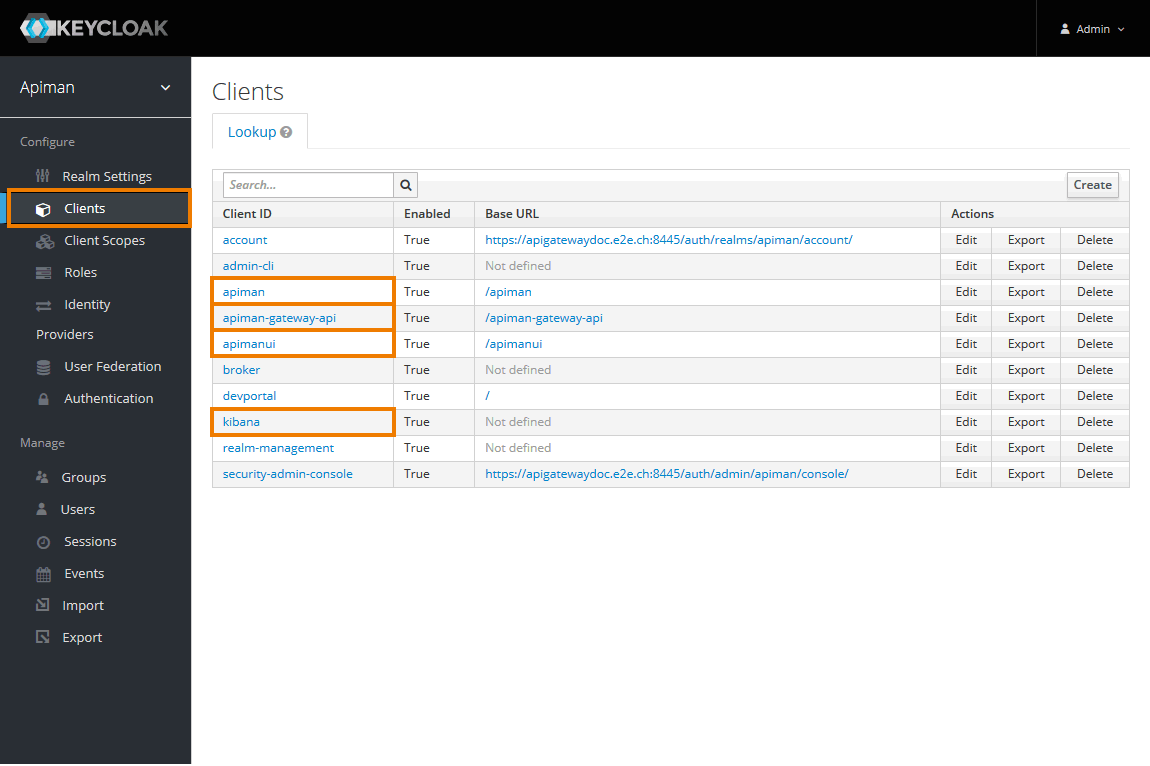 Image Added
Image AddedNavigate to Clients.
You will have to change the settings for the following clients:
- apiman
- apiman-gateway-api
- apimanui
- kibana
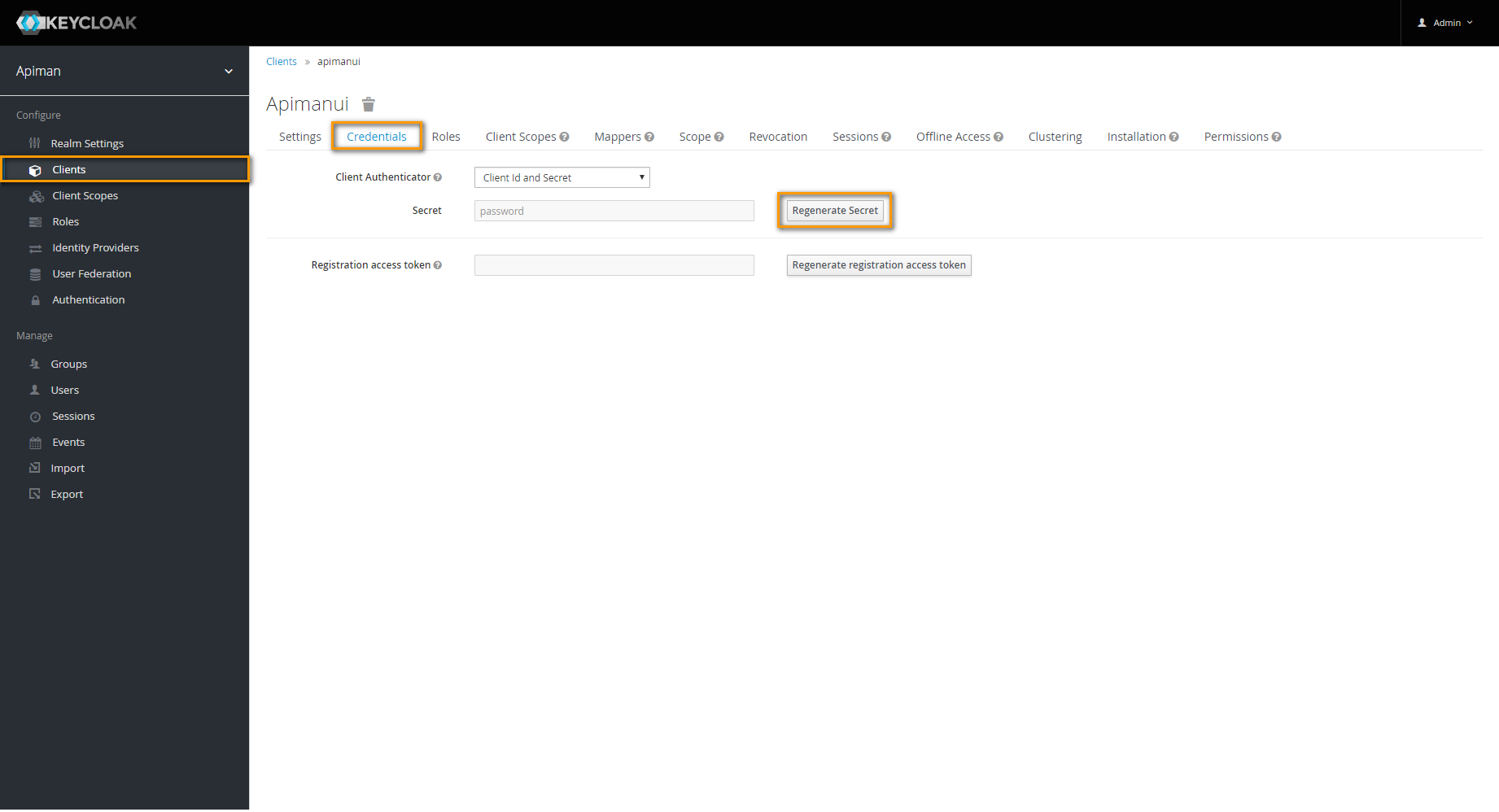 Image Added
Image AddedFor each client, go to tab Credentials and click Regenerate Secret.
In the Docker .env file,
- set the generated secret for client apiman to entry
KEYCLOAK_APIMAN_SECRET. - set the generated secret for client apiman-gateway-api to entry
KEYCLOAK_GATEWAY_SECRET. - set the generated secret for client apimanui to entry
KEYCLOAK_APIMANUI_SECRET. - set the generated secret for client kibana to entry
KEYCLOAK_KIBANA_SECRET.
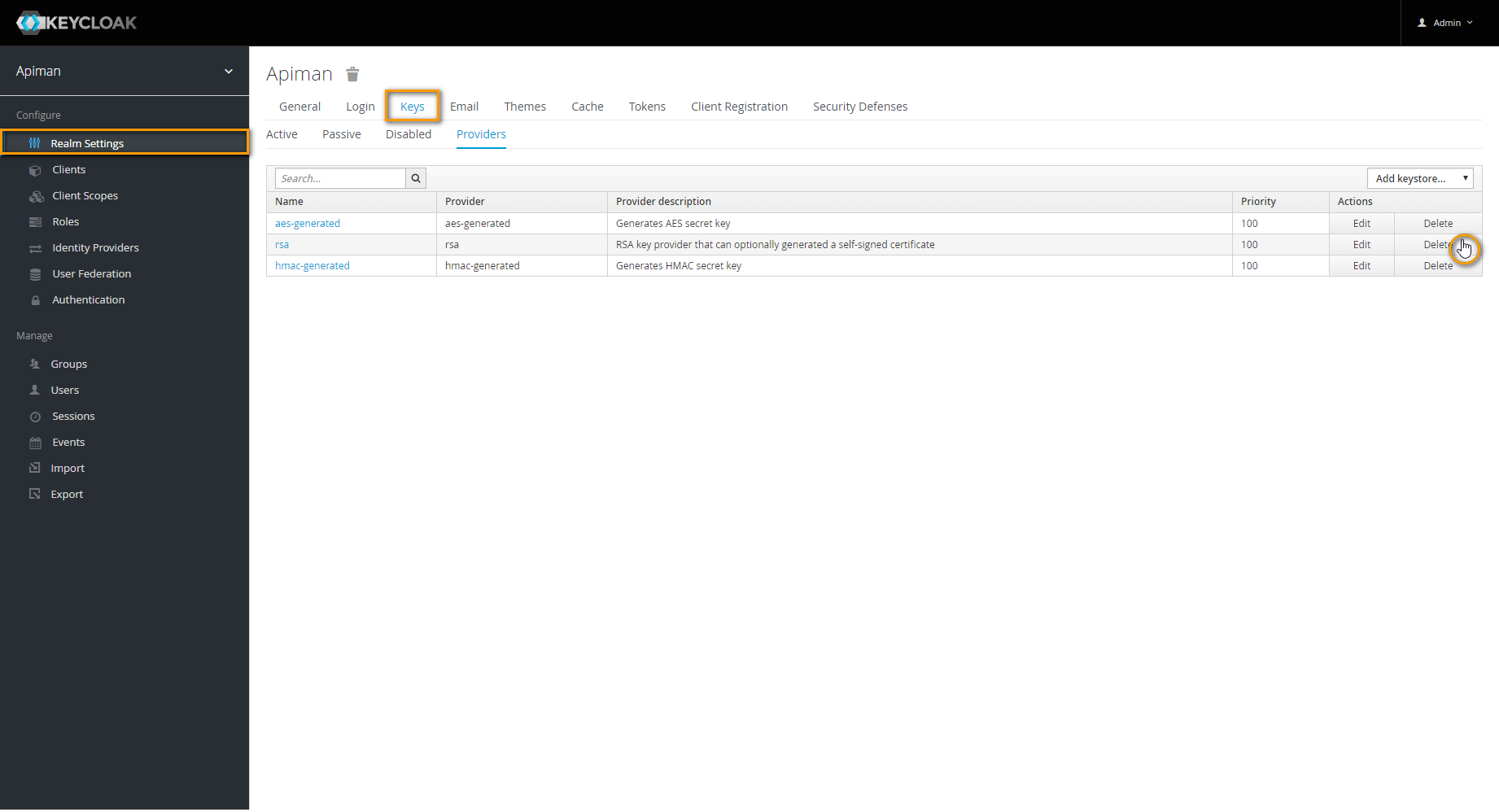 Image Added
Image AddedIn Realm Settings go to tab Keys.
Navigate to tab Providers and delete provider rsa.
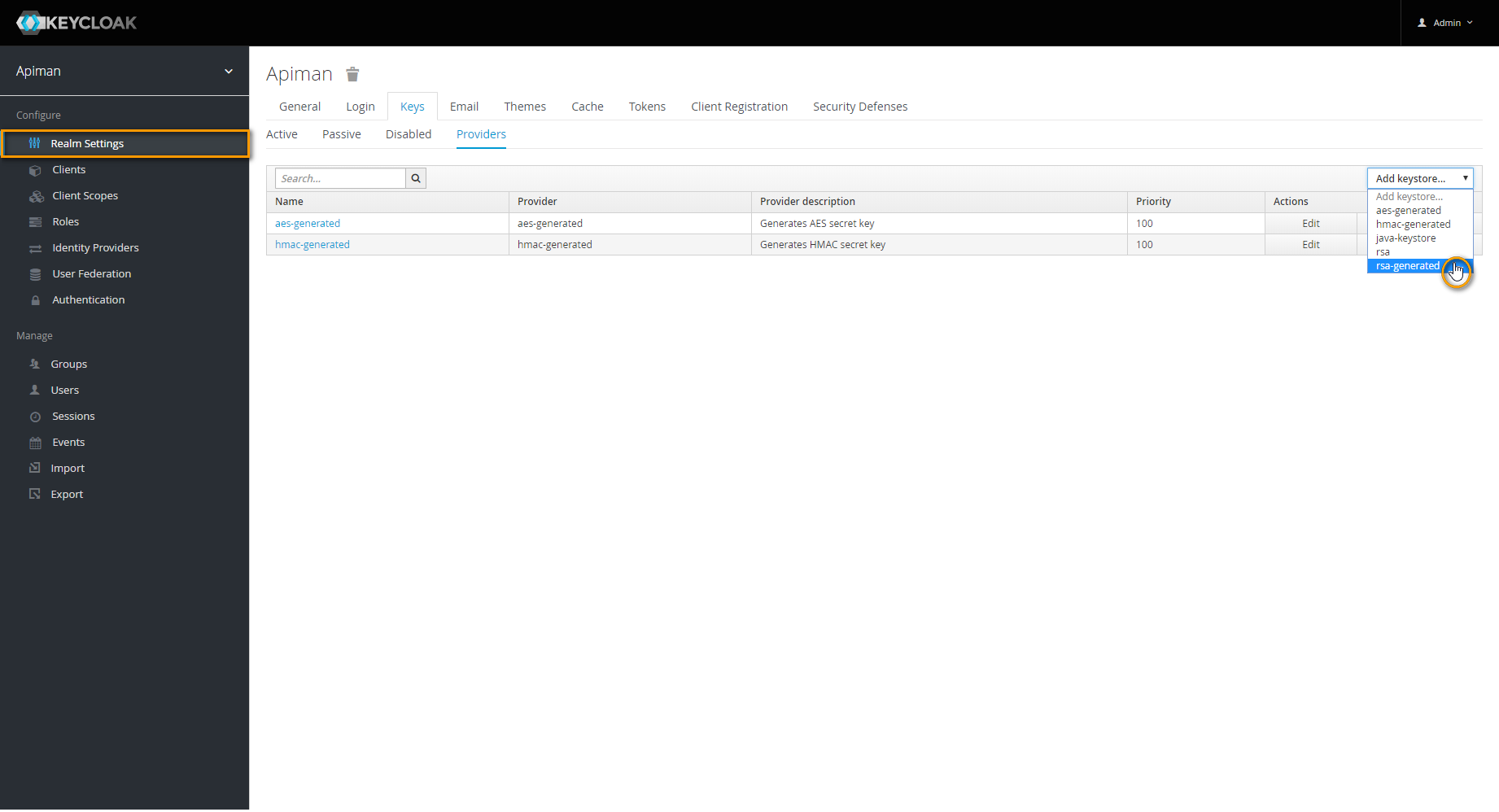 Image Added
Image AddedNext, choose rsa-generated from select box Add keystore.
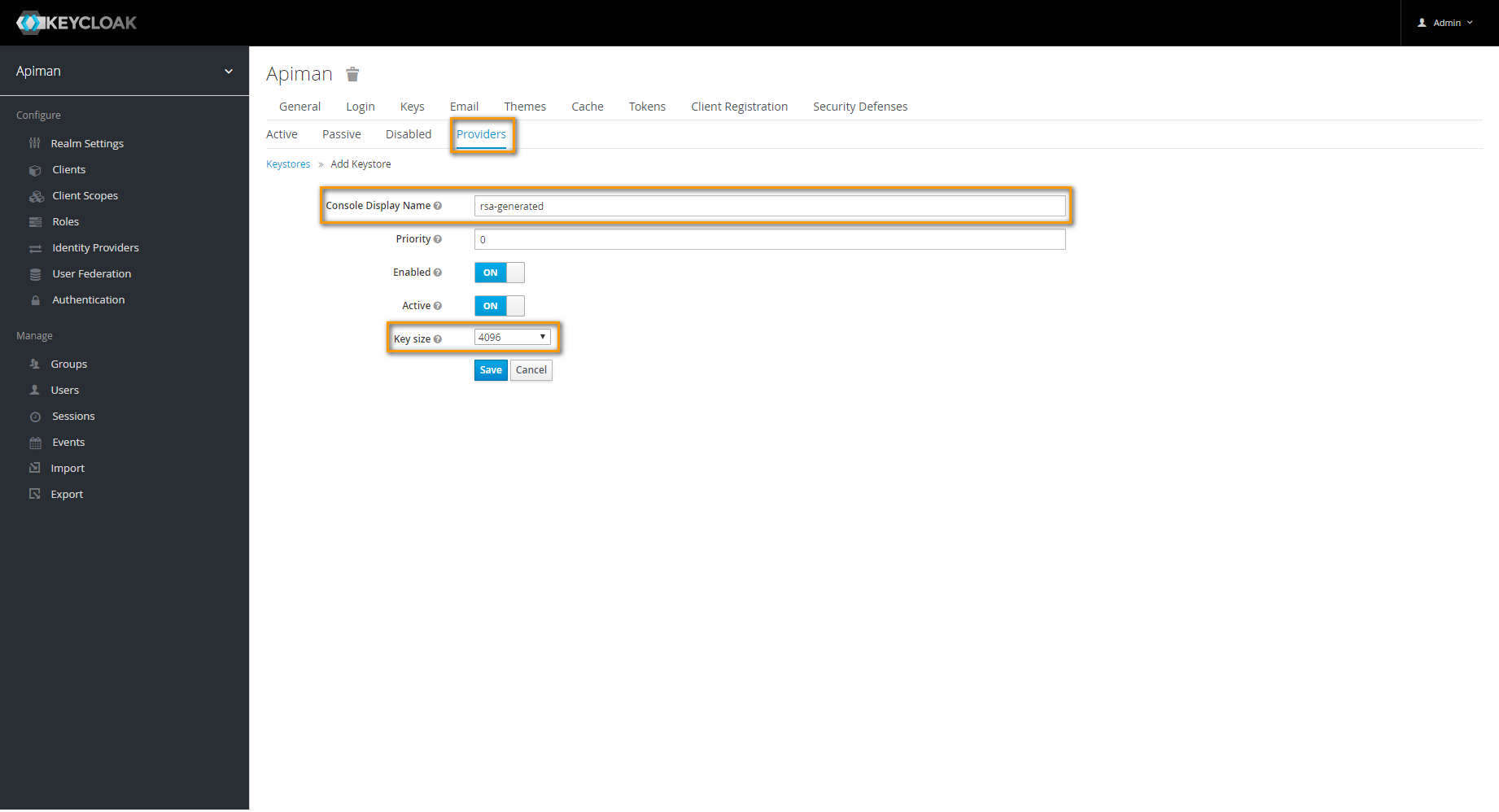 Image Added
Image AddedIn the upcoming dialog, set Key size to the maximum available value and save your changes. 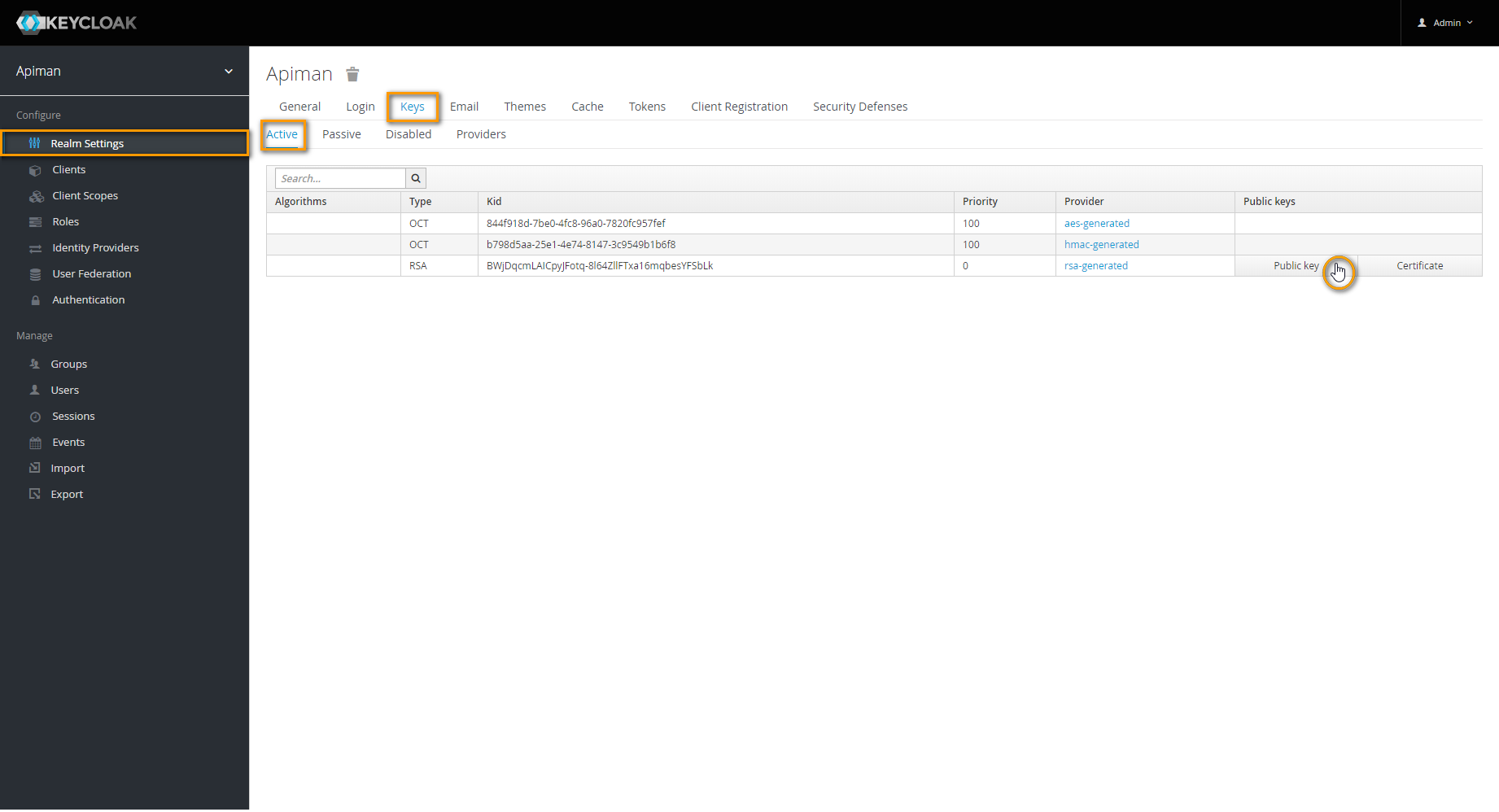 Image Added
Image AddedGo back to tab Active and click Public key.
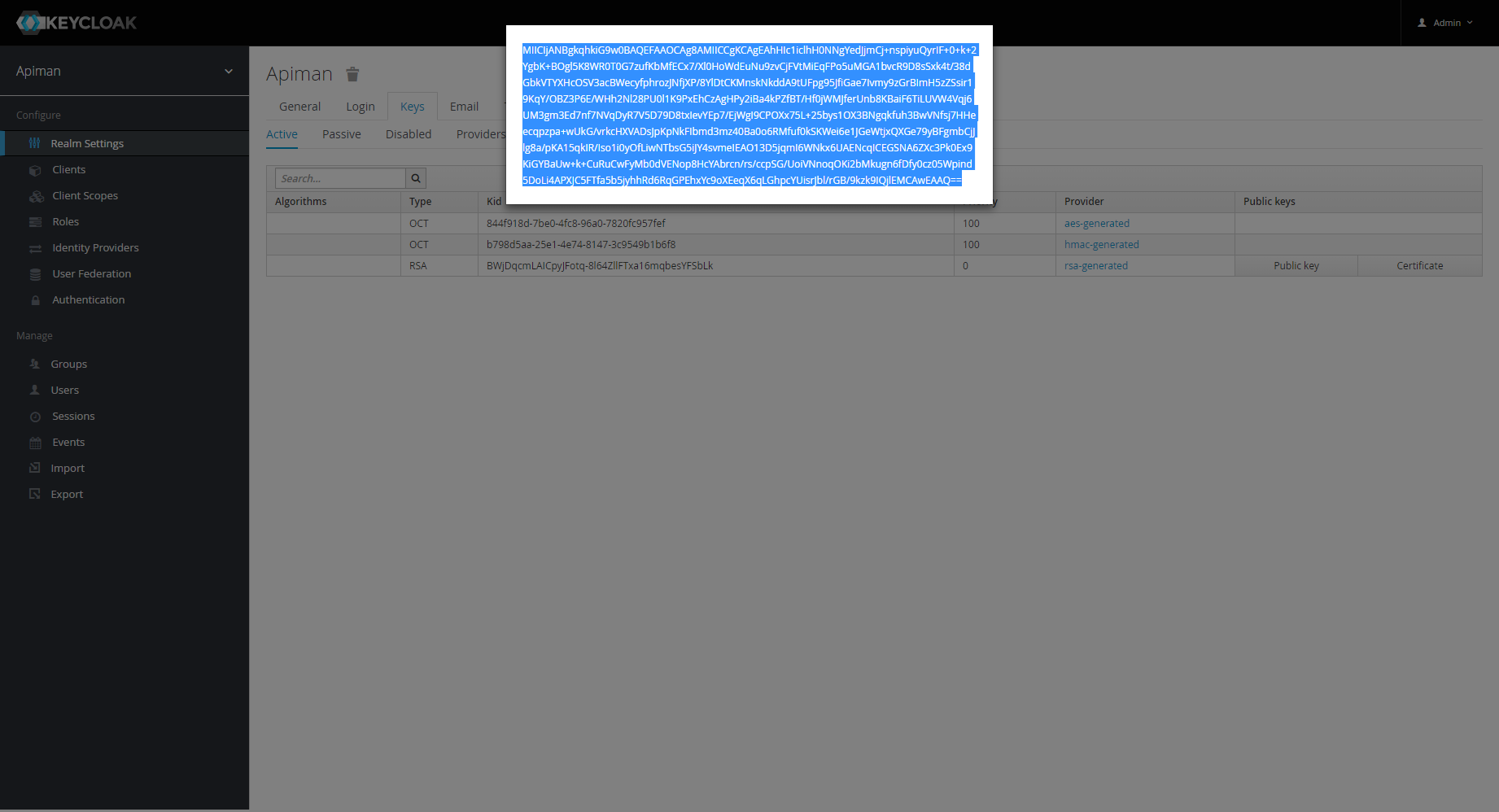 Image Added
Image AddedThe key will be displayed in a separate pop-up window.
Copy the key and paste it to variable
KEYCLOAK_REALM-PUBLIC_KEYin the Docker .env file.
| Anchor | ||||
|---|---|---|---|---|
|
All Keycloak-related settings have been configured now, and you need to stop docker-compose and restart all containers.
Stop the Keycloak container by pressing Ctrl-C.
Check the configuration, if necessary.
Tip You can check, if everything has been configured, with
Code Block docker-compose configThis command will list the Docker configuration and will throw warnings, if something is still missing.
Now start the containers. You can start all containers (including Kibana) or all containers except Kibana.
Go to folder api-mgmt/single-host-setup (folder that contains the file docker-compose.yml).
Multiexcerpt include MultiExcerptName start_all_containers_docker PageWithExcerpt INTERNAL:_installation_excerpts To start all containers except Kibana, use:
Code Block docker-compose up ui gatewayor
Code Block docker-compose up -d ui gateway
| Anchor | ||||
|---|---|---|---|---|
|
| Info |
|---|
Starting all services (previous step) may take some time. If the UI is not available yet, just wait a moment. |
Open the URL of your API Management, e.g. https://api.acme-corp.com:8443 and log in with the standard administration user, which is admin/admin.
Change the admin password to a new one of your choice as demanded on first login.
Upload the initial configuration of API Management.
To do this, go to Administration > Export/Import and import file api-mgmt/configs/bootstrap/apiman-default-config.json from api-mgmt-<VERSION>.zip. If you did not transfer the file to your client in step1, transfer this file now.Info If you want to restore a backup, use the backup file instead of the default configuration (see page API Management Backup and Restore for details).
Test the connection between UI and gateway.
To do this, go to Administration > Manage Gateways and click on the name of the gateway. Then, click Test Gateway.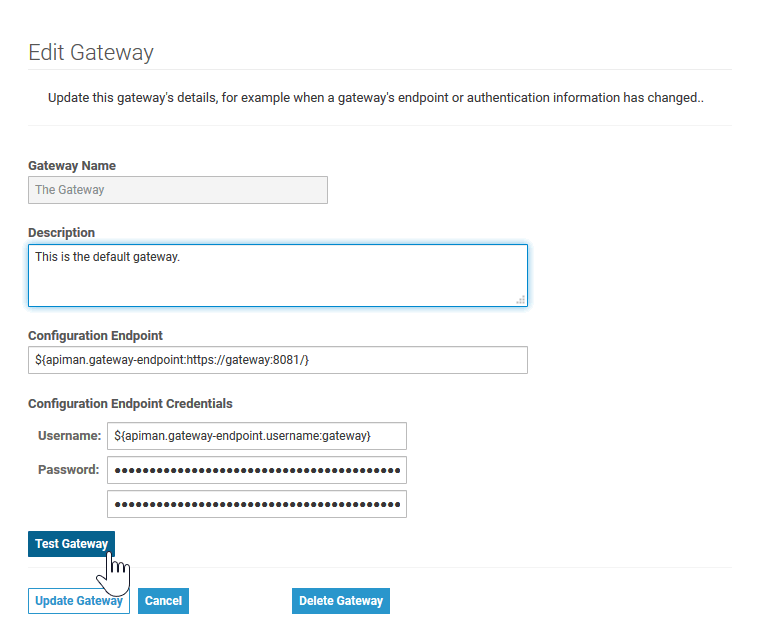 Image Added
Image AddedMultiexcerpt include MultiExcerptName test_gateway_ok PageWithExcerpt INTERNAL:_api_excerpts Multiexcerpt include MultiExcerptName test_gateway_nok PageWithExcerpt INTERNAL:_api_excerpts Note A technical user (gateway/gateway) connects the UI of API Management with the gateway. It is highly recommended to change the default passwords for both, the admin user and the gateway user. Both passwords can be changed in Keycloak.
Further Configurations
- Advanced Settings
Please refer to Advanced API Management Settings for an explanation of some additional advanced settings that can be configured for API Management. Kibana
If you want to use Kibana for your reports on API Management metrics, you may want to proceed with Setting-up Kibana.Info However, as Kibana get be setup any time after having installed API Management, we recommend to configure API Management first and record some API data, before using Kibana.
| Panel | ||
|---|---|---|
| ||
|
| Panel | ||
|---|---|---|
| ||
| Panel | ||
|---|---|---|
| ||
Docker: Elasticsearch: | ||
| Rp | ||